


If you celebrated Christmas, there was always the twinge of doubt as a kid whether you were on Santa’s Nice list, (or Naughty perish the thought). Now, you get to have that same feeling, but this time it’s Google making the list starting in January. And whether you are involved in managing a website or just “colateral damage”, you might get the digital equivalent of coal in your stocking.
How Google Chrome is Pushing the Move to More Secure Web Browsing
In 2014, Google started putting forward the idea that all web communications should be secure. They backed this up by using a pages security as a factor in its search ratings and called on the community to move to encrypted communications. The goal of this proposal is to more clearly display to users that HTTP provides no data security.
We, the Chrome Security Team, propose that user agents (UAs) gradually change their UX to display non-secure origins as affirmatively non-secure.
Back in September, Google announced that their upcoming release of Chrome 56 will start noting which sites were not secured by SSL. Chrome use is estimated at 74% browser Market. Google’s announcement is only supposed to affect pages that contain credit card information and password fields. Supposedly, this will be posted page by page, but an insecure note will also appear on the top level page of the site. In addition, Google is going to report insecure warnings on sites that looking for those sites that are secured by Sha-1 due to the vulnerability of the algorithm. Now, the deadline is almost here.
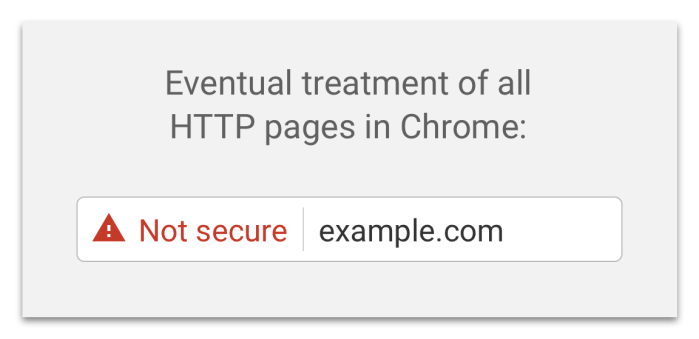
This will be followed up by Google’s call that will report only digital certificates that meet it Certificate Transparency by October 2017
For most larger companies, that run their own websites and have security programs, they probably already have updated their sites, although there are examples to the contrary. The people these enhancements might see a greater impact are small businesses, small non-profits and bloggers who might be running their own sites and have not thought about securing them, or it is not offered in their current hosting plans.
What our your options?
Do Nothing
Maybe you don’t care that your site will be branded as insecure, move down the search ranks, or you don’t do ecommerce. That might be okay for now, Google’s plan is to eventually block all non-secure traffic. So far, there has been no announced date when it will be implemented.
Purchase a Certificate
Depending on your hosting company, many hosting companies offer the . I have seen them run from $50 to $300 per year. If you have multiple domains, some of these vendors offer package deals . There are also the traditional services like Verisign and Entrust who have been creating and verifying certificates for decades. If you do purchase one, make sure that they will adhere to Certificate Transparency.
Obtain a free certificate from a Certificate Authority
There are several options to obtain a free SSL certificate. Let’s Encrypt one of the fastest growing options, is an open certificate issuing authority is run by the Internet Security Research Group (ISRG) It is supported by a number of companies including Cisco, HP, Mozilla, Facebook, Shopify, GoDaddy, Squarespace, and Google Chrome. The impact of Let’s Encrypt on the SSL certificate market on the SSL certificate market is having a sizable impact. According to Let’s Encrypt, they have issued over 5 million certificates. While there might not be an economic charge, it does not come without a cost. The certificate is for non-commercial use and is only valid for 3 months meaning that you would need to renew it 4 times a year. Let’s Encrypt says that this is by design to ensure that unused and unmanaged certificates are expired relatively quickly.
Installing and requesting a Let’s Encrypt Certificate
Usually, certificate installation requires some technical expertise. To set up a Let’s Encrypt certificate you need to to install Git, the source code management tool. I was doing this work on a Ubuntu test server that was set up to host websites. The Git install was a little bumpy because a number the required packages that Git assumed would be on the server were not present. Once I ironed out the issues with Git, I was ready to start the Let’s Encrypt install.
The Let’s Encrypt install comes down to three steps:
- Clone the Let’s Encrypt Git package
sudo git clone https://github.com/letsencrypt/letsencrypt
- Install the Lets’ Encrypt installation files
./letsencrypt-auto –help
./letsencrypt-auto –apache -d your domain name
The command above is if you are installing on an Apache webserver. There are options for nginx, webroot, and a standalone option as well.
You need to accept their Subscriber Agreement before the certificate request will continue. Once accept the agreement, you will also have to make a decision whether you will force all traffic to be HTTPS or if you will allow a combination of HTTP and HTTPS. This decision is a little more complicated considering Google’s plans to ensure make the Internet more secure.
- Allowing HTTPS traffic only can be more disruptive to your users initially, but users who have bookmarked your site or hyperlinked to it might find that their links no longer work. (You can makes changes to the .htaccess file on your server to re-point HTTP traffic to HTTPS).
- Allowing a combination of HTTP and HTTPS traffic exposes your site to Google’s crackdown on HTTP and “insecure” algorithms, which there is no set schedule.
I liken it to whether you prefer to peel the band-aid off slowly with less pain longer or just rip it off and get the pain over with.
Let’s Encrypt recognizes that the most people not really excited about having to manually renew their certificates every three months so there is a command line statement that can be set up as an automated job. They offer instruction on how to set it up in their User Guide.
How this affects You
Forewarned is forearmed . If you are a Chrome user, you will most likely see this play out in some fashion. It won’t happen all at once either. It will roll out as people start to update their browsers .So whether its little red lines showing up on your browser or a security message on your browser where you expected page information to be, it is another little annoyance that we must endure in constantly connected, and always under attack world of Cyberspace.







 NYS DFS Bucks the Trend to Keep NY Residents Cyber-Secure
NYS DFS Bucks the Trend to Keep NY Residents Cyber-Secure






